The Q-Day: A real threat to classical encryption or science fiction?
The Q-Day is the hypothetical day when a quantum computer powerful enough to break widely used classical encryption finally emerges. It marks a potential turning point in digital security — the moment when much of today’s encrypted data could, in theory, be exposed. When the effectiveness of the algorithms and a powerful enough quantum computer converge and meet, will we even know when the Q-Day has been reached?
There is much speculation about when that day might come — if ever. One researcher at Google, Craig Gidney (2025), has examined historical estimates of how many qubits would be required to break such encryption. His findings reveal a striking trend: the estimated number of qubits has dropped exponentially over time due to a better understanding of how quantum computers work in combination with optimized quantum algorithms. The most powerful quantum computers to date are reaching 1,000-10,000 qubits, which means that the gap is closing quite fast, and as the encryption we are still using is heavily reliant on the RSA-2048 cryptosystem in many applications, the threat is real, as long as the data is not migrated to a post-quantum safe cryptosystem.
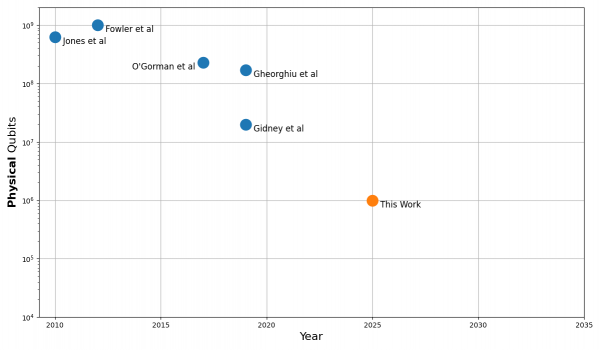
Figure: Predictions of the number of physical qubits needed in a quantum computer to break 2048-bit RSA encryption over time (Gidney, 2025)
One could extrapolate an estimate for a potential Q-Day based on these findings but first, let’s backtrack a bit to look at why this is such a hot topic and what kind of implications it might have on businesses, especially from a strategic point of view.
Post-quantum cybersecurity is a branch of cybersecurity focused on protecting data against attacks from both classical and quantum computers. By employing mathematical problems so complex that no known classical or quantum algorithm can efficiently solve them, these next-generation cryptosystems are considered post-quantum safe.
Research has shown that there are quantum algorithms such as Shor’s algorithm (Shor, 1994) that, when used on a powerful enough quantum computer, can break some of the most used cryptosystems used today. Asymmetric cryptosystems are particularly vulnerable to such attacks, with the RSA cryptosystem being one of the most widely used examples.
Data is already being stolen in a scheme called “harvest now – decrypt later”, which means that malicious actors are stealing RSA encrypted data with the intent to store it until there is a way to decrypt it using, for example, Shor’s algorithm on a quantum computer. This has triggered the National Institute of Standards and Technology (NIST) to standardize the first post-quantum secure algorithms, to secure the migration towards a post-quantum cybersecurity (PQC) solution.
On a national level, the Finnish government has produced Finland’s Quantum Technology Strategy 2025-2035 (Working group for the preparation of a quantum technology strategy, 2025). In that strategy, they have set a goal that by 2027, the most critical information and information systems regarding PQC have been identified, and risk management plans have been updated on a national level. Instructions and support options for companies in the private sector to take actions to migrate to a PQC solution should also be in place by 2027, according to the report. Finland’s Cybersecurity Strategy by Paananen et.al. (2024) has also been updated to include post-quantum cybersecurity preparations and actions to ensure that if a breakthrough in quantum computing happens, the critical infrastructure is protected.
The indications are clear: the threat is real, and both international and national efforts to prepare are advancing rapidly. A crucial question remains — how can companies ensure they keep up the pace with evolving regulations and the risks that come with them? This was the main topic in the thesis “Cybersecurity in a Post-Quantum World: Strategic Implications on Securing Data Encrypted by RSA Encryption”. The conclusion of the thesis was that the threat picture is real, which was backed up by the reports and previous research in the field, and that the level of awareness, preparedness and actions taken in Finnish companies to secure the data in a scenario where the post-quantum cybersecurity threat becomes a reality is not on a sufficient level yet. Therefore, a framework using well-known tools such as SWOT and PESTLE was created by Boxström (2025) to help company leadership teams include post-quantum cybersecurity in their strategy work.
So, whether or not you believe that Q-Day will ever become a reality, my advice is this: if you are part of a company’s leadership team, you should at the very least be aware of the potential threat, assess the risks it could pose to your business, and take appropriate action based on those findings.
References
Boxström, J. (2025). Cybersecurity in a Post-Quantum World: Strategic Implications on Securing Data Encrypted by RSA Encryption. Master of Business Administration. Vaasa: Novia University of Applied Sciences.
Gidney, C. (2025). How to factor 2048 bit RSA integers with less than a million noisy qubits. California: arXiv preprint.
Paananen, R., Soikkeli, M., Starck, M., Aro, M., Kuusisto, T., Rusila, T., & Tuulensuu, T. (2024). Finland’s Cyber Security Strategy 2024–2035. Helsinki: Prime Minister’s Office.
Shor, P. W. (1994). Algorithms for Quantum Computation: Discrete Logarithms and Factoring. : Proceedings, 35th Annual Symposium on Foundations of Computer Science (ss. 124-134). Santa Fe, NM: IEEE Computer Society Press.
Working group for the preparation of a quantum technology strategy. (2025). Finland's Quantum Technology Strategy 2025–2035 - A new engine of growth and builder for a sustainable future. Helsinki: Ministry of Economic Affairs and Employment of Finland.
Short biography of the authors:

Johnny Boxström is the main author of the blog post. He has been working in product development and management since 2014, currently working in the quantum technology ecosystem, focusing on digitalization and product management.

Ray Pörn has served as the supervisor for this master’s thesis. He holds a PhD in Applied Mathematics from Åbo Akademi University and is a Principal Lecturer at Novia University of Applied Sciences, where he also leads two master’s programs in Engineering.
The blog post has been reviewed by Novia's editorial board and accepted for publication on 12.11.2025.
![]()
MBA Insights
The Novia MBA Insights blog features peer-reviewed posts authored by MBA graduates and their supervisors. Its aim is to disseminate pertinent insights and findings from MBA thesis research.
The subject matter encompasses business, leadership, digitalisation, design thinking, services, project development, and may also touch on societal issues. Posts are selected for their relevance to professionals in the field or the general public.
All blog entries undergo review by a faculty editor and subject matter experts.
We follow CC-BY if nothing else is stated.
Disclaimer: The author(s) are responsible for the facts, any possible omissions, and the accuracy of the content in the blog.The texts have undergone a review, however, the opinions expressed are those of the author and do not necessarily reflect the views of Novia University of Applied Sciences.
Posta din kommentar
Kommentarer
Inga har kommenterat på denna sida ännu